In early October 2022, Alain Aspect, John Clauser and Anton Zeilinger were jointly awarded the 2022 Nobel Prize in Physics for work each scientist performed independently of the others.
Here’s more about the scientists and their works from an October 4, 2022 Nobel Prize press release,
The Royal Swedish Academy of Sciences has decided to award the Nobel Prize in Physics 2022 to
Alain Aspect
Institut d’Optique Graduate School – Université Paris-
Saclay and École Polytechnique, Palaiseau, FranceJohn F. Clauser
J.F. Clauser & Assoc., Walnut Creek, CA, USAAnton Zeilinger
University of Vienna, Austria“for experiments with entangled photons, establishing the violation of Bell inequalities and pioneering quantum information science”
Entangled states – from theory to technology
Alain Aspect, John Clauser and Anton Zeilinger have each conducted groundbreaking experiments using entangled quantum states, where two particles behave like a single unit even when they are separated. Their results have cleared the way for new technology based upon quantum information.
The ineffable effects of quantum mechanics are starting to find applications. There is now a large field of research that includes quantum computers, quantum networks and secure quantum encrypted communication.
One key factor in this development is how quantum mechanics allows two or more particles to exist in what is called an entangled state. What happens to one of the particles in an entangled pair determines what happens to the other particle, even if they are far apart.
For a long time, the question was whether the correlation was because the particles in an entangled pair contained hidden variables, instructions that tell them which result they should give in an experiment. In the 1960s, John Stewart Bell developed the mathematical inequality that is named after him. This states that if there are hidden variables, the correlation between the results of a large number of measurements will never exceed a certain value. However, quantum mechanics predicts that a certain type of experiment will violate Bell’s inequality, thus resulting in a stronger correlation than would otherwise be possible.
John Clauser developed John Bell’s ideas, leading to a practical experiment. When he took the measurements, they supported quantum mechanics by clearly violating a Bell inequality. This means that quantum mechanics cannot be replaced by a theory that uses hidden variables.
Some loopholes remained after John Clauser’s experiment. Alain Aspect developed the setup, using it in a way that closed an important loophole. He was able to switch the measurement settings after an entangled pair had left its source, so the setting that existed when they were emitted could not affect the result.
Using refined tools and long series of experiments, Anton Zeilinger started to use entangled quantum states. Among other things, his research group has demonstrated a phenomenon called quantum teleportation, which makes it possible to move a quantum state from one particle to one at a distance.
“It has become increasingly clear that a new kind of quantum technology is emerging. We can see that the laureates’ work with entangled states is of great importance, even beyond the fundamental questions about the interpretation of quantum mechanics,”says Anders Irbäck, Chair of the Nobel Committee for Physics.
There are some practical applications for their work on establishing quantum entanglement as Dr. Nicholas Peters, University of Tennessee and Oak Ridge National Laboratory (ORNL), explains in his October 7, 2022 essay for The Conversation,
Unhackable communications devices, high-precision GPS and high-resolution medical imaging all have something in common. These technologies—some under development and some already on the market all rely on the non-intuitive quantum phenomenon of entanglement.
Two quantum particles, like pairs of atoms or photons, can become entangled. That means a property of one particle is linked to a property of the other, and a change to one particle instantly affects the other particle, regardless of how far apart they are. This correlation is a key resource in quantum information technologies.
For the most part, quantum entanglement is still a subject of physics research, but it’s also a component of commercially available technologies, and it plays a starring role in the emerging quantum information processing industry.
…
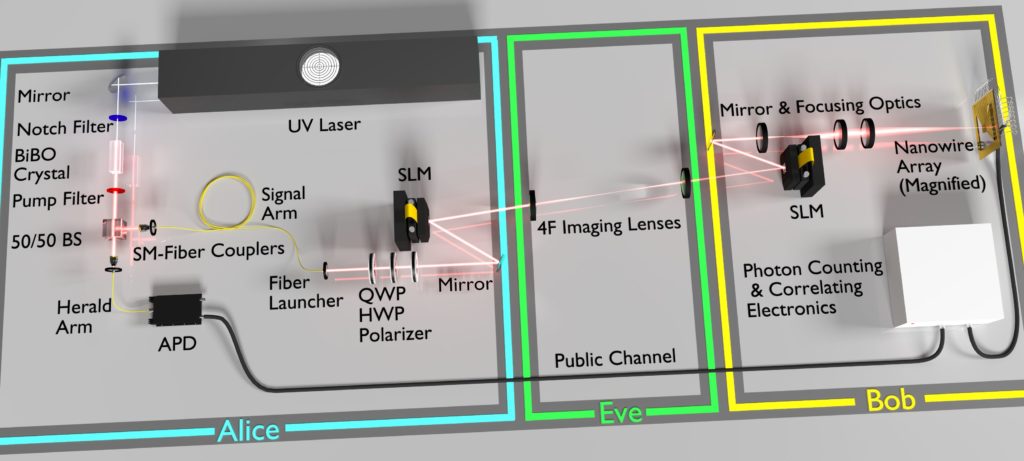
Quantum entanglement is a critical element of quantum information processing, and photonic entanglement of the type pioneered by the Nobel laureates is crucial for transmitting quantum information. Quantum entanglement can be used to build large-scale quantum communications networks.
On a path toward long-distance quantum networks, Jian-Wei Pan, one of Zeilinger’s former students, and colleagues demonstrated entanglement distribution to two locations separated by 764 miles (1,203 km) on Earth via satellite transmission. However, direct transmission rates of quantum information are limited due to loss, meaning too many photons get absorbed by matter in transit so not enough reach the destination.
Entanglement is critical for solving this roadblock, through the nascent technology of quantum repeaters. An important milestone for early quantum repeaters, called entanglement swapping, was demonstrated by Zeilinger and colleagues in 1998. Entanglement swapping links one each of two pairs of entangled photons, thereby entangling the two initially independent photons, which can be far apart from each other.
…
Perhaps the most well known quantum communications application is Quantum Key Distribution (QKD), which allows someone to securely distribute encryption keys. If those keys are stored properly, they will be secure, even from future powerful, code-breaking quantum computers.
…
I don’t usually embed videos that are longer than 5 mins. but this one has a good explanation of cryptography (both classical and quantum),
The video host, Physics Girl (website), is also known as Dianna Cowern.
If you have the time, do read Peters’s October 7, 2022 essay, which can also be found as an October 10, 2022 news item on phys.org.
I wonder if there’s going to be a rush to fund and commercialize more quantum physics projects. There’s certainly an upsurge in activity locally and in Canada (I assume the same is true elsewhere) as my July 26, 2022 posting “Quantum Mechanics & Gravity conference (August 15 – 19, 2022) launches Vancouver (Canada)-based Quantum Gravity Institute and more” makes clear.